Warning
This content has been generated by machine translation. The translations are automated and have not undergone human review or validation.
5.2.2.1 Preparing OpenSearch to Use
OpenSearch and OpenDashboards will be forked from ElasticSearch and Cabana in 2021 and are operating as separate open source projects. OCI OpenSearch is a managed service provided by OCI.
Setting policy to use OCI Search service
Granting OCI Search service permission
Allow service opensearch to manage vnics in compartment <NETWORK_RESOURCES_COMPARTMENT>
Allow service opensearch to manage vcns in compartment <NETWORK_RESOURCES_COMPARTMENT>
Allow service opensearch to use subnets in compartment <NETWORK_RESOURCES_COMPARTMENT>
Allow service opensearch to use network-security-groups in compartment <NETWORK_RESOURCES_COMPARTMENT>
Granting OCI Search Service Management Permissions in Oracle Cloud Console
- Example when the group the user belongs to is SearchOpenSearchAdmins
Allow group SearchOpenSearchAdmins to manage opensearch-family in compartment <CLUSTER_RESOURCES_COMPARTMENT>
Create an OCI OpenSearch cluster
Log in to the Oracle Cloud Console.
Go to Databases > OpenSearch > Clusters from the top left hamburger menu.
Click the Create Cluster button to create a cluster.
Select the compartment location, name, and version to create.
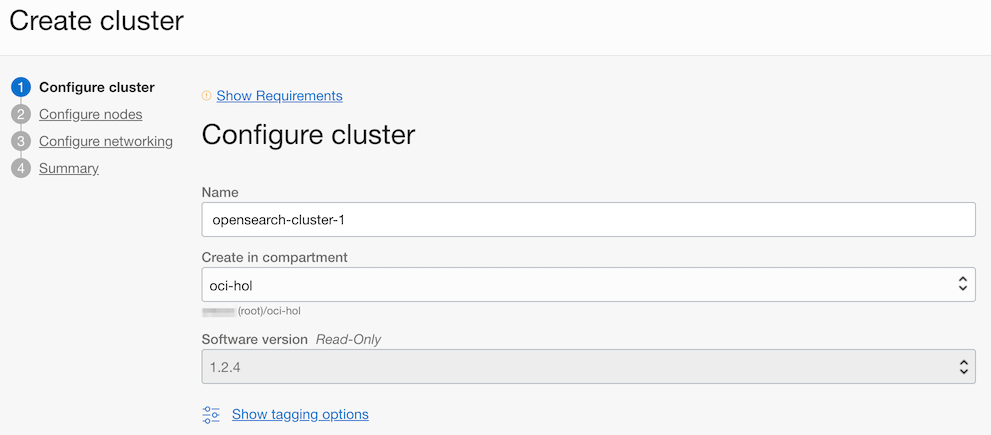
Select the node configuration to create. There are three possible configurations, here we choose the Development configuration.
- Development: 1 Master Node, 1 Data Node, 1 OpenSearch Dashboard Node
- Application Search, Log Analytics: 3 Master Nodes, 3 Data Nodes, 3 OpenSearch Dashboard Nodes
- After selecting the configuration, all node sizes can be modified. You can also change the size after cluster creation.
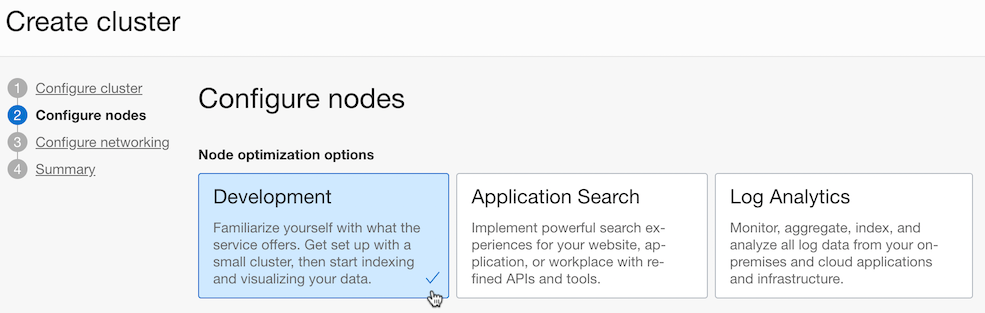
Set the subnets the cluster will use. Here, we have chosen the VCN and subnet already created when creating the OKE cluster for convenience.
Confirm the configuration information to select and create the cluster.
Based on the test date based on the development configuration, the creation time took about 20 minutes.
Created Cluster Information
- As you can see from the cluster information, both OpenSearch and OpenSearch Dashboard have only Private IP and Private FQDN. As of mid-October 2022, public IP is not yet supported.
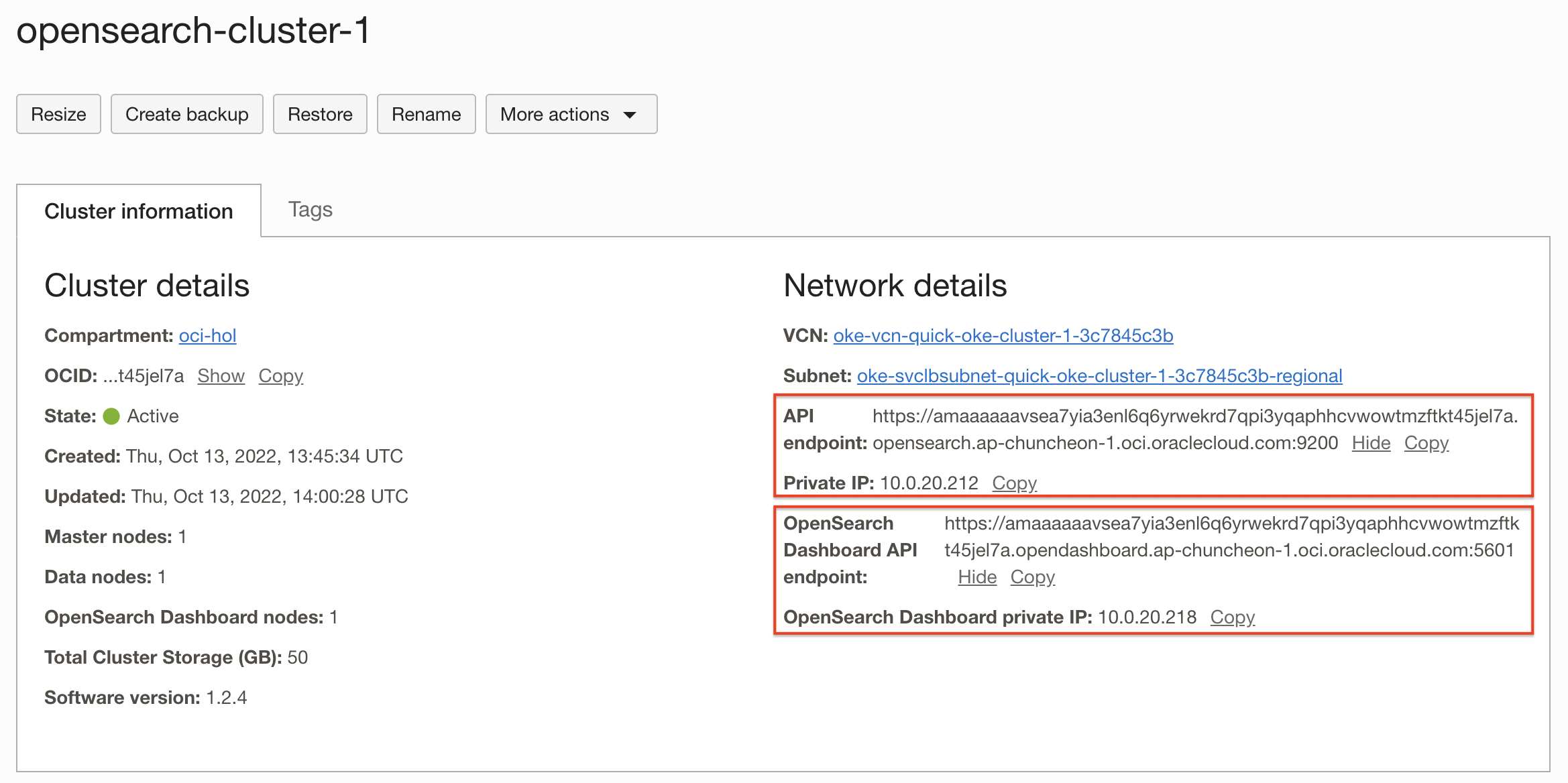
Check the OpenSearch API Endpoint, Private IP of the cluster and the API Endpoint and Private IP of the OpenSearch Dashboard.
As of September 15, 2022, the endpoint domain has been changed from oci.oracleiaas.com to oci.oraclecloud.com. And the certificate was also changed from Self-Signed certificate to DigiCert certificate. So, you no longer need to add a self-signed certificate to the client when calling the API.
- See Note in [OCI Documentation > Search Service with OpenSearch > Connection to a Cluster] (https://docs.oracle.com/en-us/iaas/Content/search-opensearch/Tasks/ingestingociopensearchdata.htm#connecttocluster)
If the cluster or endpoint domain created before September 15, 2022 ends with oci.oracleiaas.com, refer to the previous document for the integration procedure.
- [5.2.2 Log monitoring using OpenSearch based OCI Search service - Self-Signed](../../../../archives/oracle-cloudnative/oci-services/logging/2.oci-opensearch- self-signed/)
Setting up to connect to the cluster
Create a JumpBox VM
OpenSearch Dashboard does not currently support Public IP. Create additional JumpBox VM with public IP to access OpenSearch Dashboard.
In Oracle Cloud Console, go to Compute > Instances from the top left hamburger menu.
Create a new Compute VM.
Name: ex) jumpbox
Networking: Select a VCN or Public Subnet that can access the created OpenSearch cluster and assign a public IP.
Ex) In this case, we used the same network as the OpenSearch cluster we created.
Add a security rule so that the jumpbox VM can access OpenSearch from the jumpbox VM.
- Ingress Rules
- In the example below, if the jumpbox is located in the subnet 10.0.20.0/24
Stateless Source IP Protocol Source Port Range Destination Port Range Description No 0.0.0.0/0 TCP All 22 SSH No 10.0.20.0/24 TCP All 5601 OpenSearch Dashboard No 10.0.20.0/24 TCP All 9200 OpenSearch API - Ingress Rules
OpenSearch Dashboard Connection Check
Access the OpenSearch Dashboard through the jumpbox VM through SSH tunneling.
- Based on OpenSearch Cluster information, if OpenSearch Dashboard private ip is 10.0.20.218
ssh -L 5601:10.0.20.218:5601 opc@jumpboxSince SSH tunneling is done, check the connection to the OpenSearch Dashboard with a browser locally.
- Access address: https://localhost:5601
- Choose Explore on my own
As an individual, this article was written with my personal time. There may be errors in the content of the article, and the opinions in the article are personal opinions.