Warning
This content has been generated by machine translation. The translations are automated and have not undergone human review or validation.
3.5 Checking for package vulnerabilities when building DevOps services
Source Code Scanning for Vulnerability Scanning
The Application Dependency Management (ADM) service provides vulnerability scanning for library packages used to build source code within the OCI DevOps build pipeline. The build specification provides the VulnerabilityAudit type for vulnerability checking.
Currently only supports scanning for Maven packages.
Vulnerability Check Build Step
Add the VulnerabilityAudit type to the build specification and configure the related settings as shown below. To use it, you need to create a Knowledge Base in the Application Dependency Management (ADM) service beforehand.
VulnerabilityAudit example
steps: - type: VulnerabilityAudit name: "Vulnerability Audit Step" configuration: buildType: maven pomFilePath: ${OCI_PRIMARY_SOURCE_DIR}/pom.xml packagesToIgnore: - com.oracle.* - org.apache.logging maxPermissibleCvssV2Score: 10.0 maxPermissibleCvssV3Score: 10.0 knowledgeBaseId: ocid1.admknowledgebase.oc1.iad.restoftheocid vulnerabilityAuditCompartmentId: ocid1.compartment.oc1..restoftheocid vulnerabilityAuditName: testReportconfiguration/buildType: Currently only maven is supported.
configuration/packagesToIgnore: Specifies the packages to exclude from vulnerability scanning.
configuration/maxPermissibleCvssV2Score: Marks the build as Failed and aborts if the specified score is exceeded.
configuration/maxPermissibleCvssV3Score: Marks the build as Failed and aborts if the specified score is exceeded.
knowledgeBaseId: OCID of Knowledge Base in Application Dependency Management (ADM) service
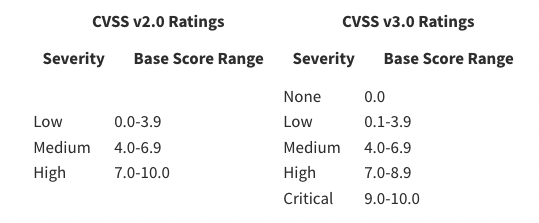
Vulnerability score
Create a Knowledge Base in Application Dependency Management (ADM) Service
Log in to the OCI console.
From the top left hamburger menu, go to Developer Services > App Dependency Management > Knowledge Bases.
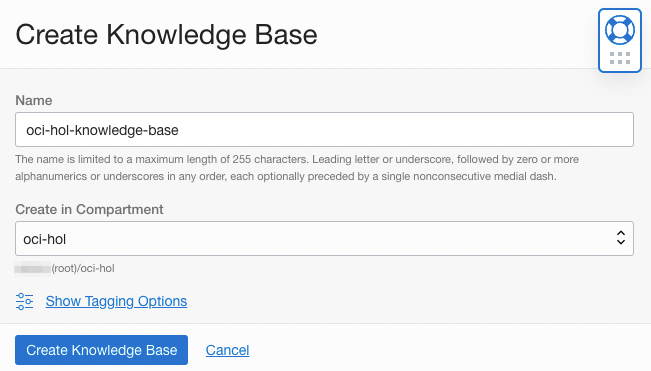
Select the target compartment and click Create Knowledge Base to create it.
- Name: Ex) oci-hol-knowledge-base
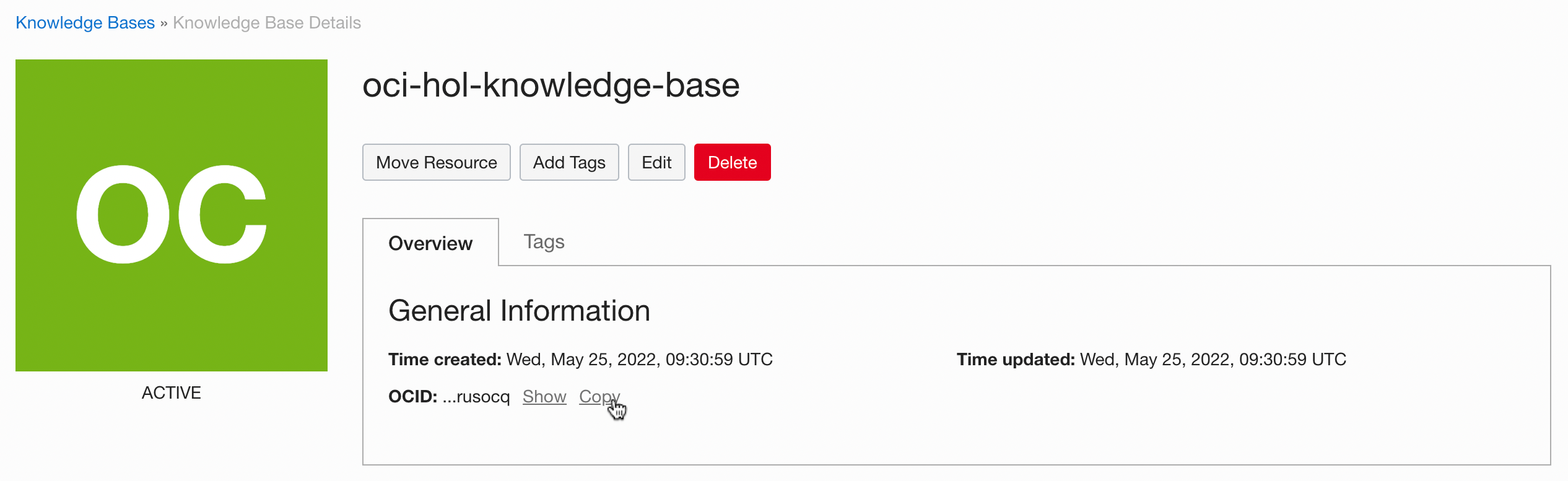
Go to the generated Knowledge Base details and copy the OCID.
Add ADM permission related policy in DevOps service
Add the following to the Policy created for DevOps.
Allow dynamic-group BuildDynamicGroup to use adm-knowledge-bases in compartment <YourCompartmentName> Allow dynamic-group BuildDynamicGroup to manage adm-vulnerability-audits in compartment <YourCompartmentName>
Create a DevOps Project
To proceed, generate the source code by following 3.1 Automating deployment of Spring Boot app to OKE using DevOps service, and Build Stage of Build Pipeline Add the following process in the state created until.
Changes for vulnerability
If you create a project with the latest Spring Boot version, there may be no vulnerabilities due to simple code. Downgrade to the older older version as shown below to force occurrence.
Lower the Spring Boot version in pom.xml of the source code. Ex) 2.6.5
... <parent> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-parent</artifactId> <version>2.6.5</version> <relativePath/> <!-- lookup parent from repository --> </parent> ...
Add Vulnerability Checking to Build Step
Define Build Spec
Define build_spec.yaml in the root path of the developed spring-boot-hello source code as follows.
build_spec.yaml
- Added a Vulnerability Audit Step step to check for vulnerabilities before building the code to the existing build spec. We set a low score to stop the build due to a vulnerability issue.
version: 0.1 component: build timeoutInSeconds: 6000 shell: bash env: variables: appName: "spring-boot-hello" exportedVariables: - APP_NAME - OCIR_PATH - TAG steps: - type: Command name: "Init exportedVariables" timeoutInSeconds: 4000 command: | APP_NAME=$appName echo $APP_NAME - type: VulnerabilityAudit name: "Vulnerability Audit Step" configuration: buildType: maven pomFilePath: ${OCI_PRIMARY_SOURCE_DIR}/pom.xml packagesToIgnore: - com.oracle.* maxPermissibleCvssV2Score: 9.0 maxPermissibleCvssV3Score: 9.0 knowledgeBaseId: ocid1.admknowledgebase.oc1.ap-chuncheon-1... vulnerabilityAuditName: spring-boot-hello-vulnerability-audit - type: Command name: "Build Source" timeoutInSeconds: 4000 command: | echo "build" mvn clean install - type: Command timeoutInSeconds: 400 name: "Build Source - Post" command: | echo "add dependency" mkdir -p target/dependency && (cd target/dependency; jar -xf ../*.jar) - type: Command name: "Define Image Tag - Commit ID" timeoutInSeconds: 30 command: | COMMIT_ID=`echo ${OCI_TRIGGER_COMMIT_HASH} | cut -c 1-7` BUILDRUN_HASH=`echo ${OCI_BUILD_RUN_ID} | rev | cut -c 1-7` [ -z "$COMMIT_ID" ] && TAG=$BUILDRUN_HASH || TAG=$COMMIT_ID - type: Command name: "Define OCIR Path" timeoutInSeconds: 30 command: | TENANCY_NAMESPACE=`oci os ns get --query data --raw-output` REPO_NAME=$appName OCIR_PATH=$OCI_RESOURCE_PRINCIPAL_REGION.ocir.io/$TENANCY_NAMESPACE/$REPO_NAME - type: Command timeoutInSeconds: 400 name: "Containerize" command: | docker build -t new-generated-image . docker images - type: Command name: "Check exportedVariables" timeoutInSeconds: 30 command: | [ -z "$APP_NAME" ] && APP_NAME=unknown [ -z "$OCIR_PATH" ] && OCIR_PATH=unknown [ -z "$TAG" ] && TAG=unknown echo "APP_NAME: " $APP_NAME echo "OCIR_PATH: " $OCIR_PATH echo "TAG: " $TAG outputArtifacts: - name: output-image type: DOCKER_IMAGE location: new-generated-image
Save the written code in the Code Repository through the git command.
git add . git commit -m "build spec" git push
test
Go to the build pipeline you created and run the build pipeline via Start Manual Run.
You can see that the vulnerability check fails during the build process.
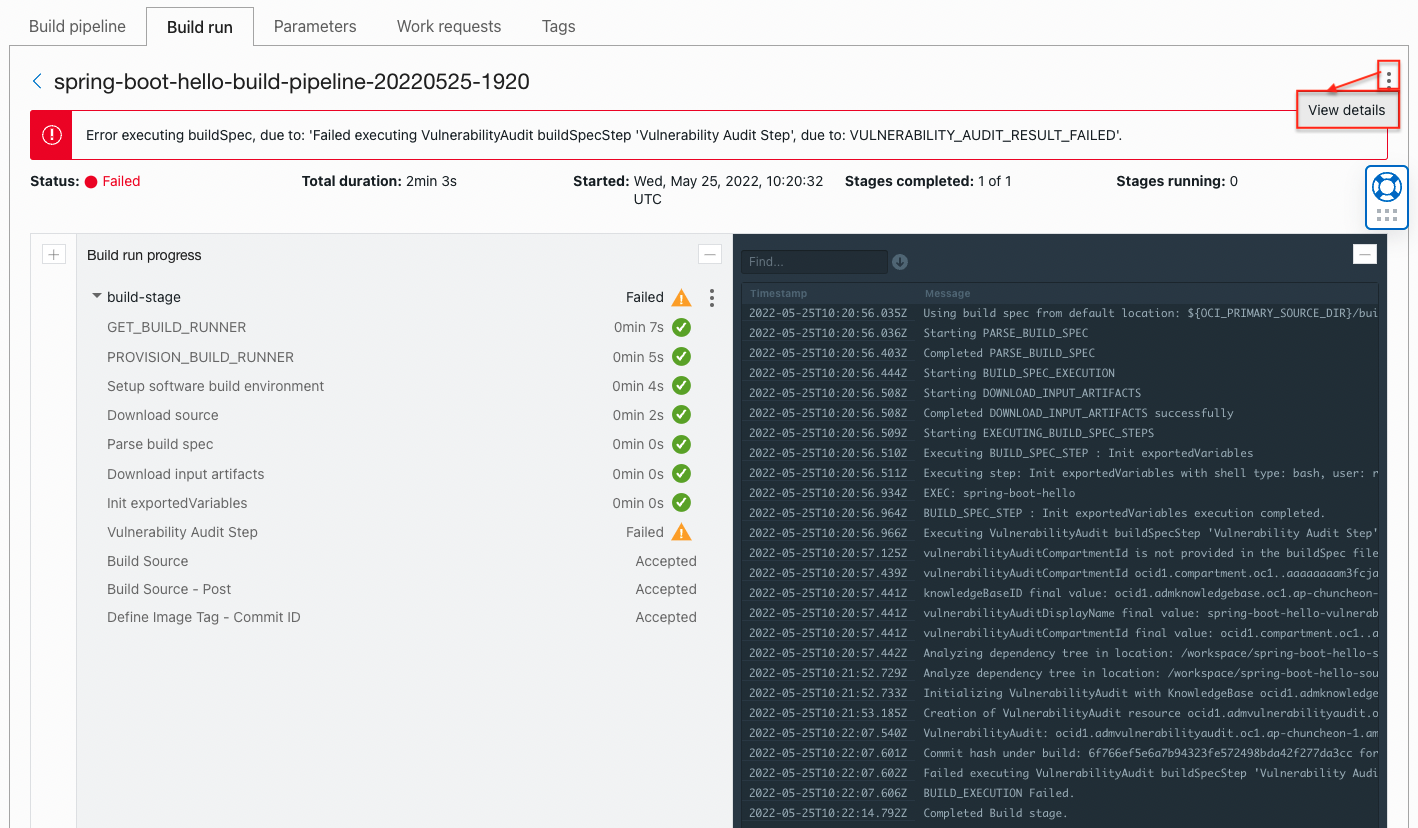
Click View Details by clicking the three dots in the upper right corner to view the details.
In Details, you can view summary information of the vulnerability scan results.
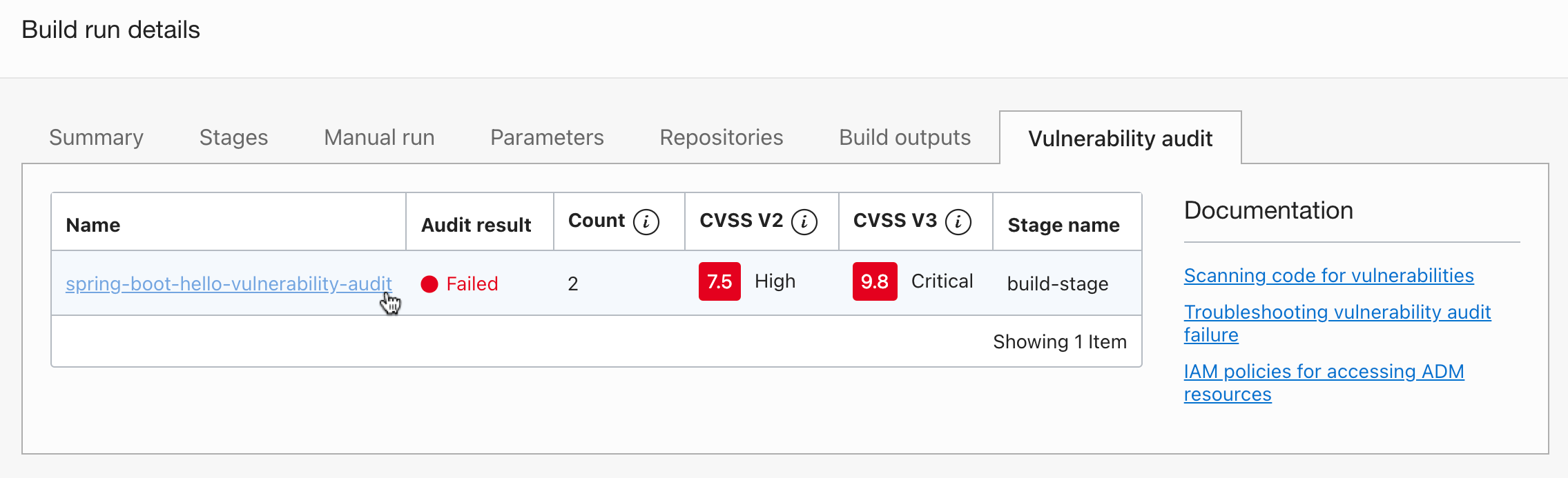
Click the report name to view the entire report.
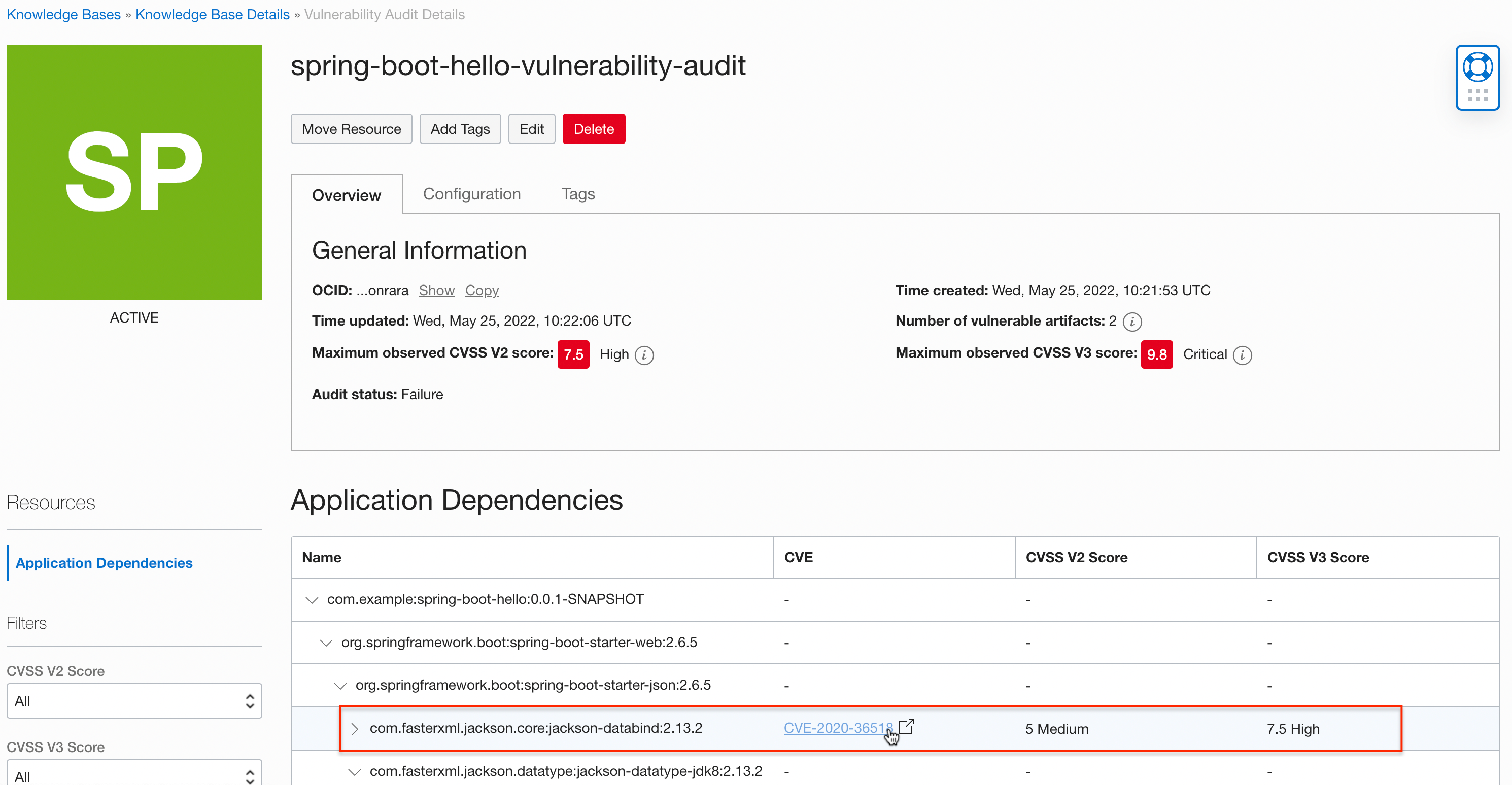
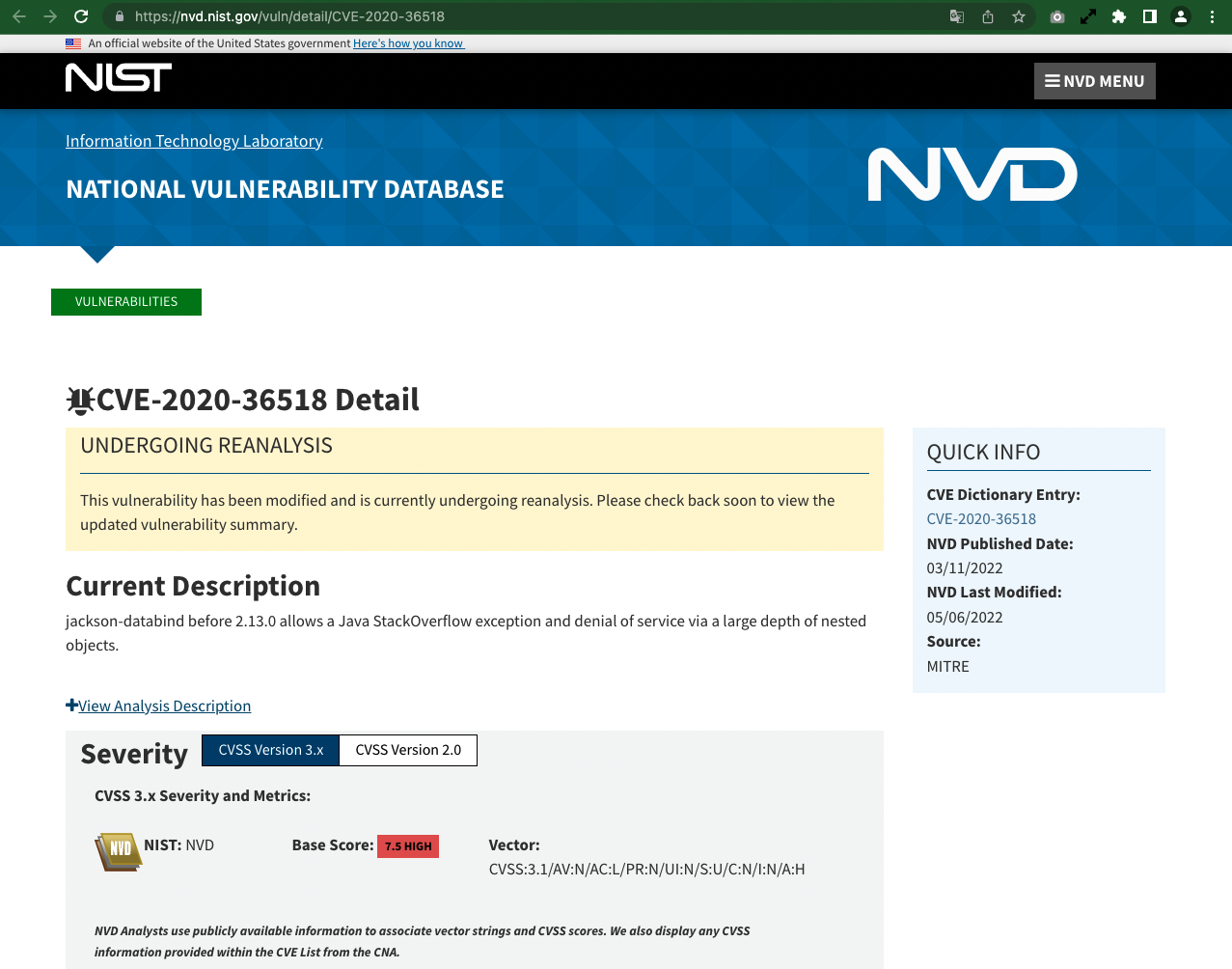
You can check the detailed information registered in the vulnerability database by clicking the vulnerability code link.
As an individual, this article was written with my personal time. There may be errors in the content of the article, and the opinions in the article are personal opinions.